# Fingerprinting
sha256: 7d7d6f46787e230d59ce6b73c39f7b63510c7a6d13a886959a27bad0f8477162
md5: e150e8abd40ad906acf19f718e610ef8
.png)
# Static Analysis
IPs/Domains: https://alor-divers.com/Nasard.xsn
Obfuscated strings are passed through a function and invoked, IEX is added on before string
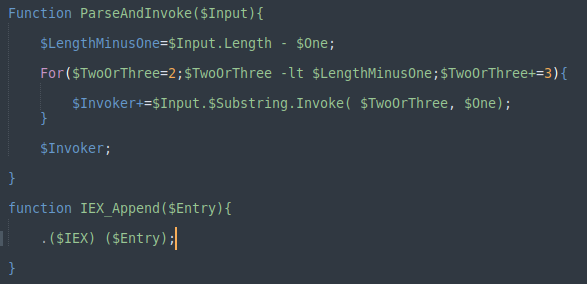
Odd path is set, seems to download some file here
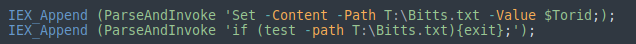
using curl or wget on the included site yeilds this. It is unclear if a malicious file used to dwell in this subdirectory

No signs of setting up persistence exist in this stage. It seems it's just the loader for a payload.
# Dynamic analysis
Not run due to suspected payload removal from site
# References
https://bazaar.abuse.ch/sample/7d7d6f46787e230d59ce6b73c39f7b63510c7a6d13a886959a27bad0f8477162/