006 - Implementing Network
Part 1 - The Network and Compute From The Ashes
I'm beginning this endeavor as RAM and other computer hardware has skyrocketed in price (December, 2025). This means some of my plans for new hardware (004 - Network Proposal V2) will need to wait until prices come down. This mainly applies to the new servers which I would like to use in my new implementation. So, for part 1 of this project I will be laying the foundational network and other work for part 2. I will start with installing my current hardware into my Mini Rack, configuring my new FortiGate 60F and my edge OPNSense router/firewall, and restructuring my PowerEdge R710 for use with network monitoring, security, and visibility tools as well as various lab environments (RHEL, AD stack, honeypots, threat emulation, etc.)
Edge Routing
For my edge router I've chosen to continue using OPNsense on my Protectli device (Outlined in 004 - Network Proposal V2). I've had no issues with it, and I've grown rather comfortable with configuring, restoring, and using the device. The 4 NIC's also serve me rather well for such a small network.
Firewall and Subnets
The firewall and subnet configuration needs to get a little creative, considering hardware limitations and my constraints set for the project. The first part to tackle was deciding what interfaces will need to be VLAN aware, setup for OSPF, or left alone. My goal throughout this entire process was to limit network downtime while configuring and designing a secure network.
At first I wanted to combine the LAN and MGT interfaces to a single VLAN aware interface and keep both on my 24p D-Link switch, however I had many issues updating firmware, configuring VLANs, SPAN ports on it. I decided to scrap that idea and keep my LAN and MGT on their own interfaces and move the MGT network to my TP-Link switch. Which was much easier to configure, and a whole lot more cooperative. My final interface configuration looks like this:
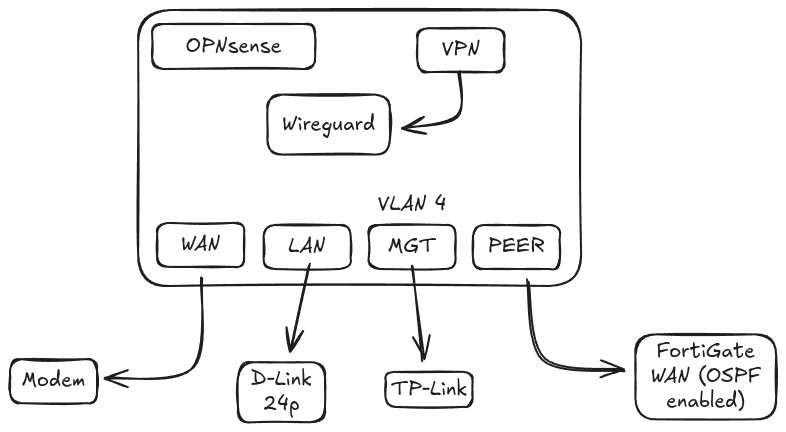
The Peer network only serves as an uplink and OSPF connection for the FortiGate. The FortiGate handles any firewall rules between the DMZ and APP subnets. However, OPNsense does manage inbound rules for the DMZ or APP networks, which ends up being easier maintainability wise, all of the outbound rules are nicely defined within interface groups or on the interfaces themselves.
Internal DNS and Certificates
Cloudflare Integration
OSPF
VPN
Adding The FortiGate
OSPF
Oddities of FortiOS
Final setup
Rebirthing the R710
The R710 will be transitioned into running internal and some external services and tooling instead of being used for my router, tooling, services, and gaming servers.
My R710 is equipped with the following:
- 2x Intel(R) Xeon(R) CPU L5640 @ 2.26GHz
- 96GB of DDR3 ECC RAM
- 4x GbE onboard ports
- Intel Dell PRO/1000 VT Quad Port NIC
- 1.75TB of storage (To be upgraded)
As time goes on I would like to make the following upgrades to the R710:
The R710 will become the primary host of my security tooling and lab environments. It has more than enough power to run everything I need it to, with some expandability storage wise for the future.
Here is a list of VM's which will be deployed on the R710:
Part 2 - One Man's Trash is Another Man's Treasure
This section is incomplete, due to the lack of cash to fund some hardware purchases. Once I obtain the hardware this section will be updated